ATLAS: Adaptable Thread-Level Address Spaces (DFG: DI 2840/1-1)
Traditionally, an OS process contains a single address space with code and data segments that are shared among all of its threads. The fork() system call creates a new address space (and process) that, even though it starts as an exact clone of its ancestor, provides strong isolation between the respective threads by means of copy-on-write.
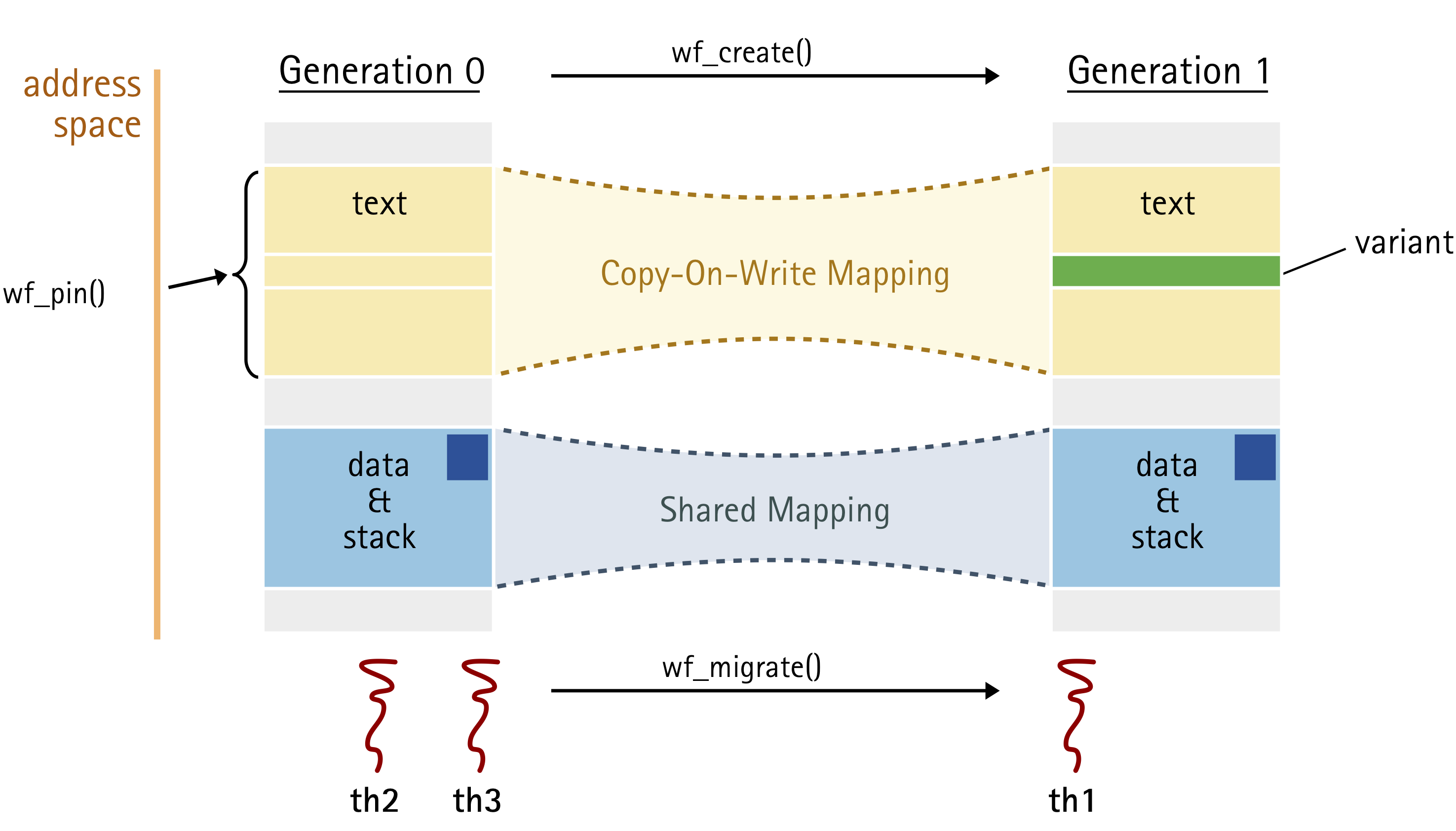
The core idea of ATLAS is to provide processes with additional address spaces that are, however, kept in sync with their ancestor: Changes to one of them – we call them address-space views – become immediately visible in the others. Views diverge only in explicitly specified areas. As they still belong to the same process, the threads of this process can be migrated individually between views.
Address-space views provide an efficient mean to implement temporary or permanent thread-level variations in the "view of the world", while threads can still interact with each other regarding the shared parts. In the figure, the code segment diverges and provides a thread-specific variation (e.g., an client-specific optimization or restriction of functionality), while the data segment is shared, so that th1 can still transparently interact with th2 and th3. Such variations can be arbitrary small or complex. They can be prepared in the background in a new view and atomically applied to individual threads by migrating them to the new address space.
Applications
In our OSDI '20 paper, we present a first application of these technique to implement WfPatch, a wait-free dynamic code-patching approch for large multi-threaded server applications.
People
Latest News
Niklas Gollenstede receives the award for the best master thesis in the field of operating systems. The award is granted annually by the SIG on Operating Systems of the German Computer Assiciation (GI Fachgruppe Betriebssysteme) solely on the base of scientific excellence. It includes a price money of 500 €. Congrats, Niklas!
For embedded systems, having a reproducible and predictable build and update process is crucial to deploy such systems in the field. In his thesis, Design and Implementation of a Light-Weight Container Runtime for Real-Time Applications, Niklas extends and improves the NixOS ecosystem to make it suitable for embedded systems. This excellent work part of the ATLAS project.

Dominik Töllner presents our paper MELF: Multivariant Executables for a Heterogeneous World at the 2023 USENIX Annual Technical Conference (ATC '23) in Boston, MA, USA. In the paper we present the Multivariant ELF (MELF) approach, which makes it possible to provide multiple per-function compile-time variants within the same binary and flexibly switch between them at run-time, optionally on a per-thread granularity. As MELFs are implemented on binary level (linker, loader), they do not depend on specific language features or compilers and can be easily applied to existing projects. In case studies with SQLite, memcached, MariaDB and a benchmark for heterogeneous architectures with overlapping ISAs, we show how MELFs can be employed to provide per-client performance isolation of expensive compile-time security or debugging features and adapt to extended instruction sets, when they are actually available. The support for MELFs is an important buliding block for our ATLAS project and also related to the ParPerOS project.

Publications
-
USENIX
Conference
A
Distinguished Artifact Award
LLFree: Scalable and Optionally-Persistent Page-Frame Allocation -
2023 USENIX Annual Technical Conference (USENIX '23)USENIX Association2023Distinguished Artifact Award.
PDF Slides [BibTex]
-
USENIX
Conference
A
MELF: Multivariant Executables for a Heterogeneous World -
2023 USENIX Annual Technical Conference (USENIX '23)USENIX Association2023.
PDF [BibTex]
-
LCTES
Conference
B
Thread-Level Attack-Surface Reduction -
Proceedings of the 24th ACM SIGPLAN/SIGBED International Conference on Languages, Compilers, and Tools for Embedded SystemsACM Press2023.
PDF Slides Video 10.1145/3589610.3596281 [BibTex]
-
SIGMOD
Conference
A*
Virtual-Memory Assisted Buffer Management -
Proceedings of the ACM SIGMOD/PODS International Conference on Management of DataACM2023.
PDF 10.1145/3588687 [BibTex]
-
LCTES
Conference
B
reUpNix: Reconfigurable and Updateable Embedded Systems -
Proceedings of the 24th ACM SIGPLAN/SIGBED International Conference on Languages, Compilers, and Tools for Embedded SystemsACM Press2023.
PDF Slides Raw Data 10.1145/3589610.3596273 [BibTex]
-
OSDI
Conference
A*
From Global to Local Quiescence: Wait-Free Code Patching of Multi-Threaded Processes -
14th Symposium on Operating System Design and Implementation (OSDI '20)2020.
PDF Video [BibTex]
Theses
Currently Running
Core-Specialized Program Execution on Heterogenous Multi-Core Processors Using Address-Space Views
Status: laufend
Supervisors: Niklas Gollenstede, Christian Dietrich
Explore new program structures that run on and fully utilize CPUs with heterogeneous ISAs.
Finished Theses
Lua as a General-Purpose Extension Language in Linker Scripts for Embedded Systems
Status: abgeschlossen
Supervisors: Niklas Gollenstede, Christian Dietrich
Embed Lua into the llvm-lld linker as a Turing-complete alternative to .ld-scripts.
Investigating the Usage and Protection of CHERI Capabilities with Shared Memory-based IPC
Status: abgeschlossen
Supervisors: Niklas Gollenstede, Christian Dietrich
Sharing virtual-address based memory capabilities between address spaces circumvents protection models. Is limiting shared memory a sufficient and appropriate counter-measure?.